Tag Archive: UC IT Blog
UC IT News
August 9, 2023
All ArticlesSurvey, UC IT Blog, UC Tech, UC Tech News, Winners

The UC IT blog team would like to thank you for participating in, and spreading the word about, our recent community survey. Thanks to you, we received over 500 responses from UC tech community members. This provided an important opportunity…
Read more about UC Tech Survey Winners Announced
UC IT Blog
June 22, 2023
All Articlesfeedback, Survey, UC IT Blog, UC Tech News

The UC IT blog news team is interested in learning more about you — who you are and how we can serve you better. Please take 1-2 minutes to complete this short survey by Tuesday, July 18 at noon.…
Read more about Your feedback needed by July 18: UC IT Blog survey
UC IT Blog
June 14, 2023
All Articlesfeedback, Survey, UC IT Blog, UC Tech News

The UC IT blog news team is interested in learning more about you — who you are and how we can serve you better. Please take 1-2 minutes to complete this short survey by Tuesday, July 18 at noon.…
Read more about Your input needed with a chance to win $75
UC IT Blog
May 25, 2022
All ArticlesRetirement, UC IT Blog, UCOP, Yvonne Tevis

By Van Williams. After nearly 34 years of UC service, Yvonne Tevis is retiring! Yvonne’s impact on the UC IT and UC Tech community cannot be overstated. She has helped build the systemwide community among technology staff across UC, most notably…
Read more about Editor of UC IT Blog, Yvonne Tevis, to Retire
UC IT Blog
October 13, 2021
All Articlescyber-risk, IS-3, policy, privacy, Robert Smith, security, UC IT Blog, UC Office of the President, UCOP

By Robert Smith. Recently, I attended an advanced training course delivered by one of UC’s IT pros. The instructor did a good job, but I noticed they were using old terms that did not align with our current electronic information…
Read more about Let’s Look Under the Hood: UC’s Information Security Policy, IS-3
UC IT Blog
November 6, 2019
All ArticlesAwards, collaboration, Events, UC IT Blog
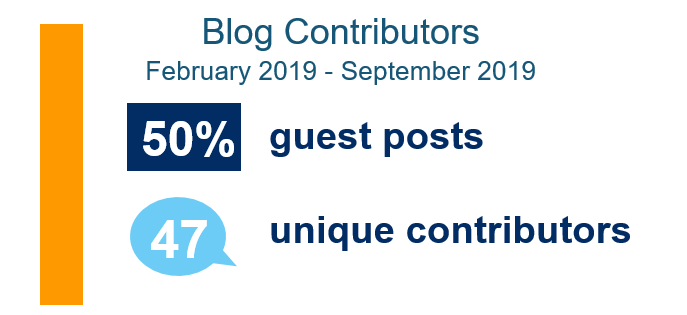
At UC, all kinds of interesting even incredible work happens in IT. We feature it in this blog – and readers provide many of the stories. That’s why we call this blog “the story of us.” If you or your…
Read more about The Story of Us – You Can Write for the UC IT Blog
UC IT Blog
June 27, 2018
All Articles, Feature ArticlesAnnelie Rugg, Sautter Awards, UC Davis, UC IT Blog, UCD
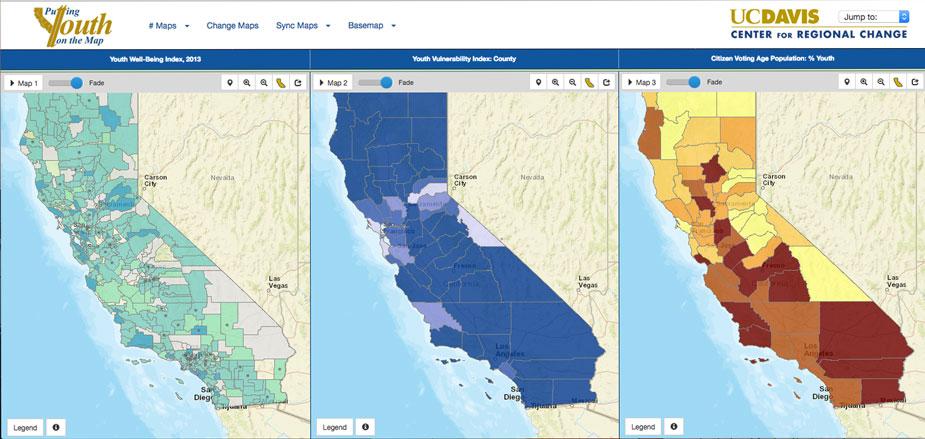
By Annelie Rugg. Behind every project are technical solutions and decisions about architecture we never hear about. In January the UC IT Blog showcased the Sautter award-winning Putting Youth on the Map (PYOM) project. Recently, I had a…
Read more about Putting Youth on the Map – How Did They Make That?
UC IT Blog
June 27, 2018
All ArticlesDede Bruno, Project Management, Slack, UC Berkeley, UC IT Blog, UCB, UCCSC

By Dede Bruno. IT project managers from across UC came together for the first time on May 17, 2018, at UC Berkeley to attend the IT Project Management Symposium: Building Bridges and Cultivating Change. Coordination of the symposium was led…
Read more about UC IT Project Managers Meet for the First Time
UC IT Blog
June 13, 2017
All Articles, Feature ArticlesSurvey, UC IT Blog, Yvonne Tevis
By Yvonne Tevis, Chief of Staff, Information Technology Services, UC Office of the President. Thanks to everyone who completed the survey! Seventy-six people responded – out of a subscriber list of 1280. Here is a summary, along with our takeaways….
Read more about The Big Reveal – UC IT Blog Survey Results
UC IT News
May 11, 2017
All Articles, Announcements/EventsReader Survey, UC IT Blog

The UC IT Blog has grown to over 1250 readers over the past two years, thanks to all of you, both readers and contributors across UC. Now we’d like your feedback to help us make the blog better and get…
Read more about Take the Reader Survey










