By Robert Smith. Recently, I attended an advanced training course delivered by one of UC’s IT pros. The instructor did a good job, but I noticed they were using old terms that did not align with our current electronic information security policy, IS-3. Just days earlier, I received a summary of an internal systemwide audit looking at the adoption of the same policy. It pointed out that UC is, overall, early in the adoption cycle. This gave me the idea for a blog post to summarize IS-3 in lay person’s terms. It’s especially appropriate this month, which is also Cyber Security Awareness Month!
Background
UC has had some kind of information security policy since 1985, before our current Gen Z students were born. From 1998 – 2011, the policy had six minor tune-ups. In 2012, UC recognized that the world had changed and a true overhaul was necessary. UC decided to move from one policy to around ten mini policies; and so workgroups were formed. While some great work was done, ultimately those projects stalled. In 2015, the project was relaunched with the idea to continue with a single policy using the international standards ISO 27001 and ISO 27002 as a reference.
The project kicked off with a workgroup in 2015. The workgroup consisted of all the CISOs and subject matter experts from around the system. The project was a priority and the workgroup met in person about once a month for an all-day working session. The group used a four-step process:
- Was the ISO 27001 requirement relevant to UC? If yes, then continue; otherwise toss it.
- Is the requirement stable and would it last five years or more? If yes, keep it in the running for the policy; otherwise consider it for a standard. (The nine standards associated with the IS-3 policy are easier to change than policy itself.)
- Could participants agree on specific language to state the requirement? If yes, write it; otherwise move on.
- Could participants agree to include the requirement? If yes, do that; otherwise, remove the requirement from consideration.
Other guideposts were that the policy had to be directly implementable and not a call for locations to write their own policies. It had to be flexible and had to cover the broad needs of the entire UC enterprise.
By January 2016, the workgroup had developed a draft policy. The CISOs and CIOs met at the Shattuck Hotel in Berkeley, CA. After some changes were made to the initial draft, the group unanimously agreed to move the policy process forward.
The next phase engaged faculty, extended stakeholders, and produced multiple drafts. This took just over a year. The final phase was the formal policy approval process. This also led to a collaboration with the Academic Senate’s University Committee on Academic Computing and Communications. President Napolitano approved the IS-3 policy, effective July 1, 2018.
The CISOs Were Right!
On September 14, 2021, Gartner reported that boards of directors now overwhelmingly view cybersecurity as a business risk.
But back in 2016, 42% of board members saw cybersecurity as a technology issue only. In just five years that shifted and by 2021, 88% of board members saw cybersecurity as a business risk!
Gartner urges organizations to rebalance accountability for cybersecurity so that it is shared with business and enterprise leaders (meaning IS-3’s Unit Heads). In reality, business leaders make decisions every day that impact the organization’s security.
In developing IS-3, the CISOs recognized that many of the decisions about technology were being made at the Unit level. UC Berkeley had been working on the idea of the Unit and Unit Head as the point of accountability, and that concept was incorporated as a central feature of the IS-3 policy. After all, Unit Heads have the influence to make cybersecurity an intrinsic value of the organization. President Drake’s security-first message is one example of this value. At the UC IT Town Hall on September 22, he stressed the importance of “doing all we can to keep … our minds focused on security.”
Thus, IS-3 embraces the notion of shared accountability for security. That means we all need to understand policy requirements and help our organizations comply.
Now Let’s Look under the Hood
At UC, knowledge and its discovery, advancement, transmission, and organization are at the heart of our mission to provide world-class teaching, research, and public service. Protecting the confidentiality, integrity, and availability of this knowledge (referred to as Institutional Information in the policy), as well as protecting our information technology resources themselves (referred to as IT Resources in the policy), are critical to support our mission.
The premise of the policy is that UC’s Institutional Information and IT Resources should be appropriately protected based on risk—that means selecting controls and making investments to manage to an acceptable level the likelihood and impact of an event. IS-3 applies to all UC Locations, to all Workforce Members, and all IT resources used to process, store or transmit Institutional Information.
Because shared language is critical for shared understanding, here are some of the most important terms and definitions from the policy:
Location: A discrete organization or entity governed by the Regents of the University of California. Locations include, but are not limited to campuses, laboratories and medical centers, health systems, as well as satellite offices, affiliates or other offices in the United States controlled by the Regents of the University of California.
Institutional Information: A term that broadly describes all data and information created, received and collected by UC.
IT Resource: A term that broadly describes information technology (IT) infrastructure and/or resources with computing and networking capabilities.
Unit: An identified point of accountability at the Location.
Unit Head: A generic term for dean, vice chancellor or similarly senior role who has the authority to allocate budget and is responsible for Unit performance.
Unit Information Security Lead: A term for the Workforce Member(s) assigned responsibility for tactical execution of information security activities including, but not limited to: implementing security controls; reviewing and updating Risk Assessments and Risk Treatment Plans; devising procedures for the proper handling, storing and disposing of electronic media within the Unit; and reviewing access rights.
Workforce Member: Employee, faculty, staff, volunteer, contractor, researcher, student worker, student supporting/performing research, medical center staff/personnel, clinician, student intern, student volunteer, or person working for UC in any capacity or through any other augmentation to UC staffing.
What Else You Need to Know
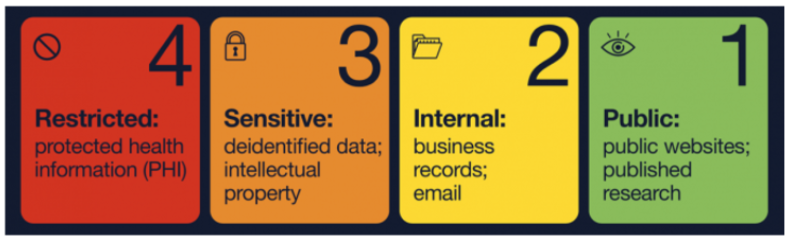
Data classification. IS-3 provides for the classification of Institutional Information into four protection levels and four availability levels. These levels range from 1, the lowest level, to 4 the highest level. See this UC IT Blog post for more details on classification. Once you determine the classification levels for your data, you can better allocate resources to protect them.
Practices. The policy also outlines practices that units should follow for:
- Identifying the key roles and responsibilities. These include:
- Developing an information security management program (ISMP) and supporting plan.
- Developing and conducting risk assessments.
Standards. IS- 3 also references nine standards to guide technical implementation. Because technology evolves rapidly, these may be updated as needed through a flexible governance model engaging the CIOs and the Academic Senate. The nine standards are:
- Account and Authentication Management Standard
- Encryption Key and Certificate Management Standard
- Event Logging Standard
- Incident Response Standard
- Institutional Information and IT Resource Classification Standard
- Institutional Information Disposal Standard
- Minimum Security Standard
- Secure Software Configuration Standard
- Secure Software Development Standard
Requirements. IS-3 presents a number of requirements that are the place to begin policy compliance, to lay the foundation, so to speak:
- Identify Unit and Unit Heads
- Develop the Information Security Management Program
- Develop the Information Security Management plan using IS-3 and the Incident Response Standard
- Create an Asset Inventory
- Create a governance process
- Risk Assessment and Risk Acceptance Processes
- Exception Process
- Risk management process guiding budgeting and planning
- Change management
Ongoing requirements include:
- Completing inventories and setting protection and availability levels
- Building in cyber risk management processes in system lifecycles
- Making sure suppliers can meet their obligations as required
- Incorporating cyber risk management into project planning
- Evaluating the current state and planning for the desired future state of cyber risk management
- Implementing and monitoring controls for effectiveness
- Developing and maintaining incident response plans
Other Features. The IS-3 policy demonstrates UC’s leadership in cyber risk management. UC’s approach is novel because the policy provides three ways to comply. Compliance can be achieved (a) by following the policy’s requirements, (b) by taking an iterative approach, and (c) by using a combination of these approaches. These options provide the flexibility that a large research university like the University of California truly needs.
Other important features of the policy are:
- A built-in exception process
- Scalability
- A CISO empowered to make key decisions related to cyber risk management
- An iterative model based on the NIST Cyber Security Framework, and one that recognizes that because locations have scarce resources, they so cannot do everything but need to apply them where there is the greatest risk (This is known as a risk-based approach.)
- A flexible application of controls based on both the Protection Level and the Availability Level, with the most controls being applied when protection and availability needs are the highest
Driving into the Digital Future
Every unit across UC must take steps to manage cyber risk. IS-3 is a flexible tool that provides a framework to address cyber-risk management. Some locations and units are far along in their journey, and some are just starting. Now is the time! Three forces are reshaping our digital world and all are driving the need for better cyber risk management. Those forces are:
- Digital Transformation. All around us technology is changing how we interact with each other and with systems. From the internet of things (IoT) to wearable medical devices, from artificial intelligence (AI) to big data, from telemedicine to the incredible innovation of our research enterprise, reliable and safe technology supports the mission. And at the same time, we are thinking more and more about the importance of our privacy.
- Bad Actors: Whether it’s cyber criminals wanting money or nation-states wanting to steal our intellectual property or surveil our community members, we are under attack. Some attacks are invisible, and some, like ransomware, can be financially or reputationally devastating.
- Expectations and Trust: Employees, retirees, patients, research subjects, students, guests, research grant agencies, and faculty all expect UC to be trustworthy stewards of their information. This means UC must use data responsibly, follow privacy principles, and practice good cybersecurity risk management. UC must excel at cyber-risk management to support its role as a world leading research university.
UC is not alone. Government agencies, banks, research partners, and others all face dramatically increased expectations for sound cyber-risk management. IS-3 is there to help guide UC in meeting those expectations.
More Information
A list of frequently asked questions is available for your review. For questions concerning implementation, please contact your location’s information security office. You can also ask questions on the UC Tech Slack channels #is-3 and #security.
The ITPS mail list will also announce upcoming webinars and new resources related to IS-12, the new IT Recovery Policy. Contact me to join the ITPS list.
 Robert Smith is the systemwide IT policy director at the University of California Office of the President.
Robert Smith is the systemwide IT policy director at the University of California Office of the President.