By Robert Smith. The University of California has a brand new information security policy!
UC President Janet Napolitano signed the policy, BFB-IS-3: Electronic Information Security Policy, on September 7, 2018.
In an increasingly collaborative world that depends upon shared electronic information, UC recognizes that it is essential to create and implement an information security policy that guides the protection and availability of our systems and data.
UC began a process of rethinking, revising, and reviewing its information security policy in 2015. The new policy is part of an overall strategy for UC to be a leader in the crucial field of cybersecurity.
UC’s approach is novel because the policy provides four ways to comply, including a lightweight Risk Treatment Plan. Compliance also can be achieved through a full risk assessment following the policy’s and related standards’ set of controls. This flexible approach is effective for a large research university like the University of California.
Other novel features are a built-in exception process, a tie to cyber insurance that links full coverage to compliance, and a flexible approach to support researchers.
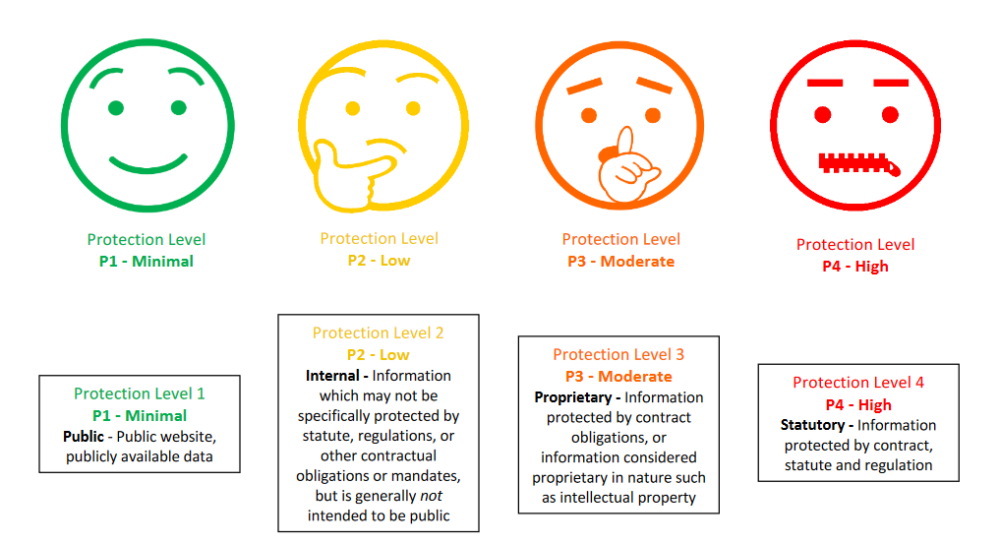
- The policy classifies institutional information and IT resources according to four “Protection Levels” and four “Availability Levels.” IS-3 and the standards set requirements so that they
- always apply, or
- apply based on one of the four protection levels (see graphic), and/or
- apply based on one of the four availability levels.
When the protection level is high, more controls are required to safeguard the institutional information. The same logic applies when there is a need for higher availability.
The policy provides the role of the chief information security officer (CISO) with considerable authority, and creates a unit-based cyber-champion called the Unit Information Security Lead.
The new IS-3 enables UC to
- protect user confidentiality,
- maintain the integrity of institutional information created, received, or collected by UC,
- meet legal and regulatory requirements, and
- ensure timely, efficient, and secure access to information technology resources.
The policy also makes security a shared responsibility by creating a single systemwide security baseline, while at the same time allowing UC locations and their units the flexibility necessary to meet their cyber-risk management needs.
Under the policy, units play a key role in planning and managing their cyber-security risk.
Additionally, nine draft standards are posted online to provide specific details on crucial topics related to information security. These will go through the governance process outlined in the new policy. They are
- Important Security Controls for Everyone and All Devices,
- Account and Authentication Management,
- Classification of Information and IT Resources,
- Disposal of Institutional Information,
- Encryption Key and Certificate Management,
- Event Logging,
- Incident Response,
- Secure Software Configuration, and
- Secure Software Development.
Two lists of frequently asked questions are available for review. For questions concerning implementation, please contact your location’s CISO.
With the adoption of the new IS-3, the prior version of IS-3 and two other policies were rescinded; these were IS-2: Inventory, Classification, and Release of University Electronic Information and IS-10: Systems Development Standards.
The revised and updated IS-3 would not have been possible without the support of an entire team, including experts in multiple fields across all UC locations who contributed, reviewed, and vetted all details of the policy. The Academic Senate also provided valuable feedback and input during the policy’s creation, ensuring that IS-3 enhances and supports UC’s mission to serve society as a center of higher learning.
Watch the UC IT Events page, the Slack channel #is-3, and the ITPS mail list for upcoming webinars about IS-3.
 Robert Smith is systemwide IT policy director at the University of California Office of the President.
Robert Smith is systemwide IT policy director at the University of California Office of the President.

I want to say congratulations and thank you to the many, many, many people who have played a role in scripting, editing, review, championing & persisting this policy through the process and across the finish line. It is a shining example of collaboration & partnership as well as an important milestone for us on our cyber journey