By John Virden. The University of California has a new systemwide electronic information security policy, often referred to as IS-3. It was signed into action by President Janet Napolitano, September 7, 2018, and is the culmination of many years of review and collaboration, including significant involvement and direction from the Academic Senate. The policy incorporates international best practices and follows a risk-based approach.
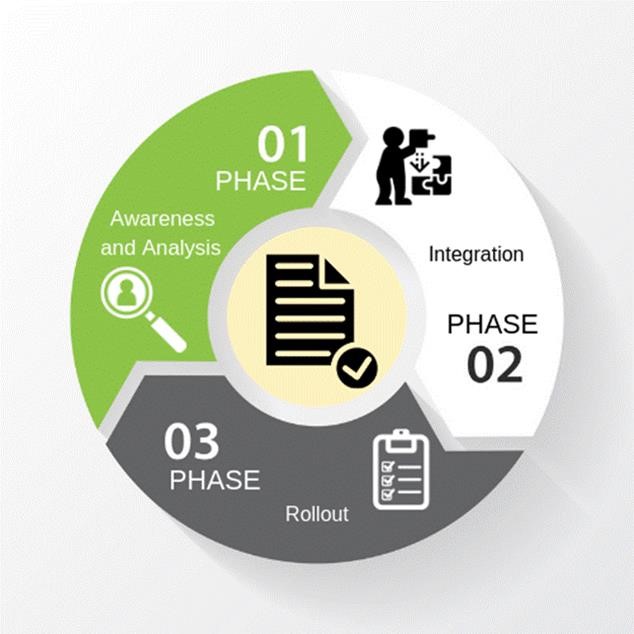
Now that we have a refreshed set of cybersecurity requirements, how do we implement them across our diverse and decentralized campuses? At the University of California, Riverside, we are fullfilling IS-3 implementation in three stages.
Phase I. Awareness and Analysis
To get a head start, while the policy was in a draft state in 2017, we created a cross-campus task force dedicated to building awareness about the future policy. UCOP and UCR policy directors joined our meetings to share the history and vision of the policy, as well as our local UCR policy system.
Working with our cyber-risk responsible executive, chief information officer, and provost, we created a cybersecurity policy approval process so we would be ready if systemwide policy necessitated additional or revised local policy and standards. Our task force also conducted a gap analysis to get a jump on any local cybersecurity policy needs not covered by IS-3. Additionally, UCR subject matter experts participated in the new IS-3 policy drafting and review efforts.
Phase II. Integration
In 2018, we started building out fundamental cybersecurity programs and decided to infuse them with the draft IS-3. Realizing the policy was still in draft form and subject to change, we remained flexible as our programs developed.
Risk assessments of new systems and software acquisitions are critical for reducing vulnerabilities and supporting a risk-based approach to information security. We remodeled our risk assessment form to include a section-by-section compliance check with the new IS-3 controls.
We revised our annual security inventory web (ASI) application to include a 31 item questionnaire. This now allows organizational checks to ensure that security programs address UC business needs, operating environments, the threat landscape, regulatory requirements, and changes in technology. Following requests from other UC campuses, we are expanding our ASI web application to allow multi-tenant use. (For more information, please contact David Gracey, UCR deputy CIO, Enterprise Solutions.)
Finally, IS-3 concepts were infused into a cloud security standard and our procurement process.
Phase III. Rollout
This phase is where the rubber meets the road. We created a UCR rollout model based on a UC Davis plan that consisted of discovery, assessment, and planning. We added a gap analysis portion, using our annual security inventory and new system security review to provide a quick IS-3 compliance check, which is essential for creating a unit security plan.
Once the compliance check is complete, a risk assessment reveals findings to reduce risk and improve the unit’s cybersecurity posture. Implementation of suggested controls may require substantial resources, including personnel, material costs, and time. Mitigation precedence is ordered based on control type (administrative, technical, physical), the NIST Cybersecurity Framework (CSF), and the Center for Internet Security’s top-twenty suggested cybersecurity actions to help eliminate cyber threats. Units will use this plan to address mitigations as resources and risk tolerance allow over the next two to three years.
Lessons Learned
During our IS-3 rollout across UCR, we had some positive learnings and also found areas for improvement.
We were impressed that our cross-campus business owners were already aware of the new IS-3 policy and how it can support their programs. They realized having a thorough policy in place quickly allows them to meet audit and compliance requirements. It also helps them with requests for enhanced security controls and measures.
It was found that security professionals easily understand the contents of IS-3, but non-security professionals still need some help interpreting how it can be implemented or how to apply safeguards. To this end, the UC Office of the President created a Quick Start Guides by Role website. It makes things easier for our population because it lists job responsibilities of workforce members, unit heads, proprietors, and chief information security officers with respect to information security.
The Unit Information Security Lead (UISL) is key to implementing IS-3 requirements in our decentralized environments, in which many independent colleges and schools have their own IT workforce. The UISL holds responsibility for the tactical execution of information security activities associated with IS-3.
Finally, we learned that a campus or location information security office is necessary to help interpret IS-3 and facilitate risk assessment for other departments on campus.
 John Virden is chief information security officer, UC Riverside.
John Virden is chief information security officer, UC Riverside.